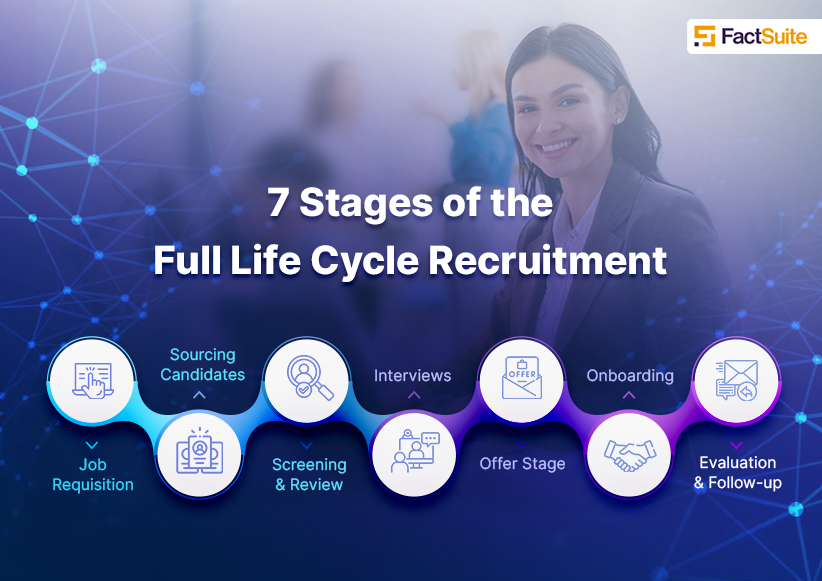
The Impact of Identity Theft: How Identity Verification Can Help Prevent It?

Table of Content
- Introduction
- Types of Identity Theft
Financial Identity Theft
Medical Identity Theft
Criminal Identity Theft
Social Security Identity Theft - Causes of Identity Theft
Hacking and Data Breaches
Phishing and Social Engineering
Skimming and ATM Fraud
Stealing Mail and Dumpster Diving - The Consequences of Identity Theft
Financial Loss
Damage to Credit Score
Criminal Records
Emotional Impact - The Role of Identity Verification in Preventing Identity Theft
Importance of Identity Verification
Different Types of Identity Verification
i.Document Verification
ii.Biometric Verification
iii.Knowledge-Based Verification
Benefits of Identity Verification
i.Increased Security
ii.Reduced Fraud
iii.Improved Customer Experience - The Future of Identity Verification in India
Aadhaar Card
Biometric Verification
Other Forms of Identity Verification - Best Practices to protect yourself from Identity Theft
Secure Passwords
Two-Factor Authentication
Regularly Monitor Your Accounts
Be Cautious with Your Personal Information - Conclusion
1.Introduction
Identity theft is a growing concern in India and around the world. It refers to a situation where someone steals your personal information and uses it to commit fraud or other criminal activities. The impact of identity theft can be devastating, causing financial losses, damage to your credit score, and a loss of trust in institutions. In this article, we will explore the different types of identity theft and their impact on individuals and society.
Identity theft is a serious problem in India, with thousands of cases reported every year. According to a report by the National Crime Records Bureau, there were 33,964 cases of identity theft reported in India in 2019. This represents a 15% increase from the previous year, highlighting the growing threat of this crime.
According to Statista, the southern state of Karnataka in India, reported the highest number of registered cases related to online identity theft in 2021, with more than 1700 cases recorded with authorities. The entire country recorded over 4000 cases of online identity theft in the same year, falling under the jurisdiction of Section 66C of the Indian Penal Code.
2.Types of Identity Theft
There are several types of identity theft, each with its own set of risks and consequences. Here are the most common types of identity theft:
Financial Identity Theft
Financial identity theft is the most common type of identity theft, where someone uses your personal information to obtain credit, loans, or other financial products. This can include credit card fraud, opening bank accounts in your name, or taking out loans using your identity. The consequences of financial identity theft can be severe, with victims often facing financial ruin and difficulty in getting credit in the future.
Medical Identity Theft
Medical identity theft is a type of identity theft where someone uses your personal information to obtain medical treatment or services. This can include using your health insurance information to get medical care or even to obtain prescription drugs. The consequences of medical identity theft can be severe, including incorrect medical records, loss of insurance coverage, and even physical harm if the thief's medical condition is mistaken for the victim’s.
Criminal Identity Theft
Criminal identity theft occurs when someone uses your personal information to commit a crime, such as fraud or theft. This can include using your identity to obtain a driver's license, apply for a job, or even commit a serious crime such as robbery or murder. The consequences of criminal identity theft can be severe, with victims often facing criminal charges or being falsely accused of crimes they did not commit.
Social Security Identity Theft
Social Security identity theft is a type of identity theft where someone uses your social security number to obtain benefits or other government services. This can include using your social security number to obtain a job, file for unemployment benefits, or even receive government benefits such as Medicare or Medicaid. The consequences of social security identity theft can be severe, including loss of benefits, difficulty in obtaining future benefits, and even legal trouble if the thief is caught.
3.Causes of Identity Theft
Hacking and Data Breaches
Hacking and data breaches are one of the most common causes of identity theft. Cybercriminals can gain access to sensitive personal and financial information by infiltrating computer systems and stealing data. This can occur through a variety of means, including malware, viruses, and phishing attacks. Once hackers have obtained this information, they can use it to commit fraud and steal money from victims.
According to a Hindustan Times publication, Union minister Ashwini Vaishnaw reported that there were approximately 59 cases of government website hacking in year 2020, 42 in 2021, and 50 cases in 2022. Additionally, there were 6 cases of data breaches in 2020, 7 cases in 2021, and 8 incidents of data breaches in year 2022.
According to CERT-In, they were able to detect and prevent 2,83,581 cases as such in year 2020, 4,32,057 cases in 2021, and 3,24,620 malicious scams during the year 2022. The attempts of cyberattacks were made from both within the country and abroad.
Phishing and Social Engineering
Phishing and social engineering are techniques that scammers use to trick individuals into providing personal information. This can occur through emails, phone calls, or text messages that appear to be from legitimate sources such as banks, credit card companies, or government agencies. The scammers may ask for sensitive information such as social security numbers, passwords, and credit card information, which they can use to commit identity theft.
Skimming and ATM Fraud
Skimming and ATM fraud occur when criminals place devices on ATMs or point of sale (POS) terminals that are designed to steal credit or debit card information. The devices can be difficult to spot and can capture the information when the victim swipes their card. The criminals can then use this information to create counterfeit cards or make unauthorized purchases.
Stealing Mail and Dumpster Diving
Stealing mail and dumpster diving are methods that criminals use to obtain personal information such as bank statements, credit card offers, and other documents that contain sensitive information. Criminals may also search through trash cans or dumpsters to find discarded documents that contain personal information. This information can then be used to commit identity theft.
4.The Consequences of Identity Theft
As per a 2021 article by India Today, a new report by NortonLifeLock reveals that 59% of Indian adults have fallen victim to cybercrime in the past year, collectively spending 1.3 billion hours trying to resolve these issues. The report surveyed over 10,000 adults in 10 countries, including 1,000 adults in India, and found that 36% of Indian adults detected unauthorized access to an account or device in the past year, while 45% experienced identity theft. Of these victims, 14% were impacted in the past year alone, indicating that over 27 million Indian adults experienced identity theft in the past 12 months.
Here are some potential consequences of Identity Theft:
Financial Loss
One of the most significant consequences of identity theft is financial loss. Victims may lose money from their bank accounts, have credit cards opened in their name, or have loans taken out in their name without their knowledge. This can result in significant financial hardships for victims.
Damage to Credit Score
Identity theft can also damage a victim's credit score. When fraudulent accounts are opened in a victim's name, the payments that are missed or the balances that are not paid can negatively impact the victim's credit score. This can make it more difficult for victims to obtain credit in the future.
Criminal Records
Identity theft can also result in victims having criminal records. Criminals may use a victim's personal information to commit crimes such as fraud, theft, or even terrorism. This can result in significant legal issues for victims, including fines, imprisonment, and difficulties finding employment.
Emotional Impact
Identity theft can have a significant emotional impact on victims. It can cause feelings of vulnerability, anger, and betrayal. Victims may also experience depression and anxiety as a result of the crime.
5.The Role of Identity Verification in Preventing Identity Theft
Identity theft is a growing concern for individuals and organizations alike. The rise of the digital age has made it easier for fraudsters to steal personal information and use it for malicious purposes. As a result, identity verification has become an essential tool in preventing identity theft. In this article, we will explore the importance of identity verification, the different types of identity verification, the benefits of identity verification, and the future of identity verification in India.
Importance of Identity Verification
Identity verification is the process of confirming that an individual is who they claim to be. It is crucial in preventing identity theft and other types of fraud. Identity verification is used in a variety of settings, including banking, healthcare, and government services.
Different Types of Identity Verification
There are various methods of identity verification, including document verification, biometric verification, and knowledge-based verification.
i. Document Verification
Document verification involves verifying a person's identity by examining their official documents. These documents could include passports, driver's licenses, or national identity cards. The person's name, photograph, and other personal details on the documents are cross-checked against a database of authorized documents. Document verification is widely used in the banking and financial sectors.
ii. Biometric Verification
Biometric verification is a method of identity verification that uses physical characteristics to identify individuals. These physical characteristics could include fingerprints, facial recognition, or iris scans. Biometric verification is considered to be a highly secure method of identity verification.
iii. Knowledge-Based Verification
Knowledge-based verification involves asking individuals questions that only they would know the answers to. For example, questions about their previous addresses or their mother's maiden name. This method of identity verification is commonly used in customer service settings.
Benefits of Identity Verification
Identity verification has many benefits. These benefits include increased security, reduced fraud, and improved customer experience.
i. Increased Security
Identity verification ensures that only authorized individuals have access to sensitive information. It also helps to prevent fraudulent activity.
ii. Reduced Fraud
Identity verification is an effective way to reduce fraud. It prevents individuals from using stolen or fake identities to gain access to services or carry out illegal activities.
iii. Improved Customer Experience
Identity verification can improve the customer experience by making it faster and more convenient to access services. Customers can quickly verify their identities without having to go through lengthy processes.
6.The Future of Identity Verification in India
India has implemented several initiatives to improve identity verification in the country. The most notable of these initiatives is the Aadhaar Card.
Aadhaar Card
The Aadhaar Card is a biometric identification system that assigns a unique identification number to each Indian citizen. The Aadhaar Card contains biometric information, such as fingerprints and iris scans, as well as demographic information, such as name and address. The Aadhaar Card is used for a variety of purposes, including government services and financial transactions.
Biometric Verification
Biometric verification is becoming increasingly popular in India. The use of biometric technology is expected to increase in the future as it is a highly secure method of identity verification.
Other Forms of Identity Verification
Other forms of identity verification, such as document verification and knowledge-based verification, will continue to be used in India. However, biometric verification is expected to become the dominant form of identity verification in the country.
7.Best Practices to Protect Yourself from Identity Theft
Protecting yourself from identity theft has never been more critical. Identity theft is a significant problem that can lead to substantial financial losses and other damages. It is essential to take precautions to protect yourself from identity theft. In this article, we will discuss the best practices to protect yourself from identity theft.
Secure Passwords
One of the most important things you can do to protect yourself from identity theft is to create secure passwords. Weak passwords are easy to guess, and cybercriminals can easily crack them. It is crucial to create strong passwords that include a mix of letters, numbers, and symbols. It is also essential to use different passwords for different accounts. That way, if one account is compromised, your other accounts will still be secure.
Two-Factor Authentication
Another way to protect yourself from identity theft is to use two-factor authentication. Two-factor authentication is an extra layer of security that requires a user to provide two forms of identification. This could be a password and a code sent to your phone or email. Two-factor authentication makes it much harder for cybercriminals to gain access to your accounts.
Regularly Monitor Your Accounts
It is crucial to monitor your accounts regularly to catch any fraudulent activity as soon as possible. You should check your bank statements, credit card statements, and any other financial statements regularly. If you notice any unauthorized transactions, report them immediately to your bank or credit card company. Most financial institutions have fraud departments that can investigate suspicious activity.
Be Cautious with Your Personal Information
Another way to protect yourself from identity theft is to be cautious with your personal information. Do not give out personal information over the phone, through email, or on social media. Cybercriminals can use this information to steal your identity. You should also shred any documents that contain personal information before throwing them away.
Beware of sharing your identity proof or pictures on WhatsApp for a job, loan, or other purposes as it could be a trap. Sumit Khanna, a resident of Hargobind Nagar, had his identity proofs tampered with and used to take six loans worth Rs 4 lakh from three banks and three finance companies. He discovered this when he received a call from ICICI Bank about a two-wheeler loan he had not availed. Upon visiting the bank, he found out that his identity proofs were misused by someone who had availed the loan in his name. This is an incident from 2022 and has been reported by The Tribune.
8.Conclusion
Identity theft is a serious problem that can cause significant financial and personal damage. The best practices to protect yourself from identity theft include creating secure passwords, using two-factor authentication, regularly monitoring your accounts, and being cautious with your personal information.